
I have seen this twice now in the past few weeks and – I’ll put money on it – no doubt I’ll be seeing it again soon.
The scam I’m about to describe is called .LOCKY and it has already caused the permanent destruction of many millions of personal computer files around the world.
Let me tell you why this is such a concern to me and why you need to know about this. Here’s how it works.
Firstly, it has to find its way on to your computer. That is incredibly easy today. Despite all the warnings to the contrary, people still open email attachments and people still download files. And that’s all it takes.
Both of the incidents I came across recently were caused by opening a Word document attached to an email. Both were opened because the subject line said: ‘You haven’t paid this invoice yet..’ and both clients wanted to find out which ‘invoice’ the email was talking about. But, when this Word document is opened a piece of software (called a Word Macro) gets run in the background and that is all that’s necessary to kick off the whole process.
Unknown to the user, at this point, his antivirus software may be disabled and all of his personal files, including pictures, word documents, excel spreadsheets, powerpoint presentations, pdf documents and many others, are now encrypted and, while this is going on, there are no visible signs of anything wrong.
Only when the rogue software has finished the encryption process, does it make its presence known. That is when you get presented, on your screen, with a ransom note. Basically this says: “Your files have been encrypted. If you ever want to see them again, send the money (usually around £300 – £400) to … “ [followed by payment instructions]. You will also notice now that you cannot open any of your files and they have all had their names changed to some random set of characters and a file extension of .LOCKY.
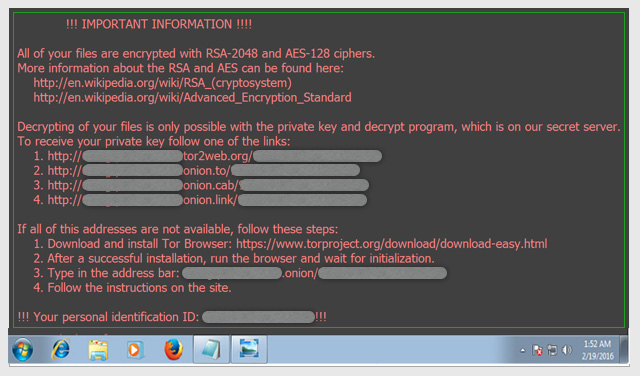
Now the first thing to realise is that, if you actually follow the instructions and pay the ransom, there is absolutely no way you can be sure you’ll actually get your files decrypted again. In fact, I’d say your chances are less than 50-50 at best. After all, the criminals have already got your money. They are still completely anonymous. Why would they want to stay involved to keep their side of the bargain?
The second thing to realise is that, without the ‘encryption key’, you will not be able to decrypt your files yourself and nor will anyone else – no matter what they may tell you. The encryption software is very strong (so-called military grade) and even Governments with supercomputers and access to the best decryption resources in the world could struggle. So your encrypted files have gone. Get used to it. Your only chance of recovery is to find old copies that may have been missed by the encryption process – or backups.
And that, of course, is the beauty of regular backups. Because if you backed up your C: drive the night before and the external drive you backed up to was removed from your computer, you will get all your files back from there. All you need to do is have your computer professionally cleaned up to eradicate the rogue software and then restore your files from the backup device.
But there may still be a real problem here. What if you only have one backup device and it was connected to the computer when the encryption was in progress. It is possible (though currently unlikely) that your backup may have also been encrypted (or even destroyed) at the same time. This really concerns me because very few domestic computer users take proper backups in the first place but, even among those who do, even fewer, have more than one backup destination, remove the backup device after use and store good backups offline. But this needs to become the new norm. It’s what IT departments around the world have been doing for businesses since computers were invented.
So what do you do?
The only real answer to this is to ensure you have a solid, robust backup strategy in place and that you understand it. You can talk to us about this. Call us or email. See our About Us page.

